- John The Ripper Crack Excel
- John The Ripper Crack Hash Linux
- John The Ripper Crack Hash
- John The Ripper Crack Sha1 Hash Value 1
John the Ripper password cracker. Using John for cracking single hashes Thanks a bunch.It works now.What are the avaliable formats that I can use? As PWDUMP'ed.
I'm using John the Ripper version 1.7.8 on Linux Ubuntu to crack Linux user passwords as an exercise. I run the Linux on a virtual machine. I created a user called 'User1' to the system and set a password 'axby' for it. Then I got the password hash with the usual command:
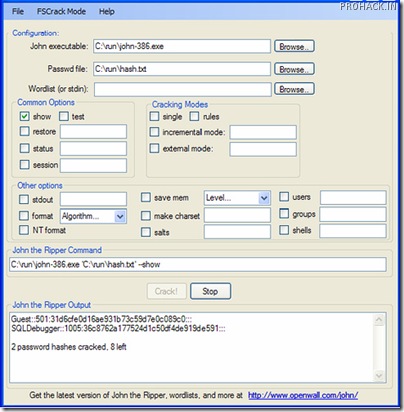
Windows password cracking using John The Ripper. In this post I will show you how to crack Windows passwords using John The Ripper. John the Ripper is a fast password cracker, primarily for cracking Unix (shadow) passwords.Other than Unix-type encrypted passwords it also supports cracking Windows LM hashes and many more with open source contributed patches. John the Ripper password cracking tool - How to use Step by step guide IT Security. Now copy the hash value as shown in fig -1 and save it in the notepad. ==> Time to crack this hash root@Shield:~# john /root/Desktop/john.txt --format=raw-sha1 Note: /root/Desktop/john.txt is my directory where i have save this file.
Then I run John with command:

As I'm writing this question the program has run like 30 minutes trying to guess a simple 4-letter password. Is this normal? Or have I done something wrong? Any suggestions to speed things up would be appreciated.
John the Ripper's command line syntax. Allows you to override the hash type detection. As of John the Ripper version 1.8.0, valid 'format names' are descrypt. John The Ripper Hash Formats John the Ripper is a favourite password cracking tool of many pentesters. There is plenty of documentation about its command line options. I'm trying to crack some MD5 hashes given in OWASP's BWA on their DVWA site. I was able to use John the Ripper and the very first time it worked fine and it showed the reversed hashes using the cod.
fixer1234closed as too broad by Ƭᴇcʜιᴇ007, nerdwaller, Xavierjazz, Dave M, DavidFeb 6 '14 at 1:39
Please edit the question to limit it to a specific problem with enough detail to identify an adequate answer. Avoid asking multiple distinct questions at once. See the How to Ask page for help clarifying this question. If this question can be reworded to fit the rules in the help center, please edit the question.
1 Answer
Yes, that is pretty common since John uses either a Dictionary Attack or Brute-force. Neither of which are terribly fast, especially against many modern hashing algorithms running on a single thread (running some hashes is expensive, as @DavidSchwartz mentions).
John without arguments also uses pretty slow methods, from the FAQ:
Q: How long should I expect John to run?
A:It primarily depends on the cracking mode(s) and on your password files (in particular, the type of hashes and the number of different salts, if applicable). Most importantly, you should note that the 'incremental' mode, which a default John run (with no command line options) proceeds with after being done with the quicker checks, is not supposed to terminate in a reasonable time.
One option to try to squeeze out better performance is to enable parallelization with --fork=N (N is number of processes) or --node. See the options list for details on those.
Theoretically, if you have two threads running semi-intelligently - your execution time should be cut in ~half. (Note the qualifier 'theoretically', YMMV in the real world)
Not the answer you're looking for? Browse other questions tagged ubuntupasswords or ask your own question.
Join GitHub today
GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together.
Sign upHave a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Comments
commented Jan 25, 2016
referenced this issue Jan 25, 2016
Added format for 16bytes-RawSHA1 AxCrypt in-memory secrets commented Jan 25, 2016
That commit doesn't work for me Probably trivial problem though. |
commented Jan 25, 2016
Have you enabled any of the two tests? If so, they will work fine if you try to crack them in a real run. I tested this here and on super. This error means self test ciphertext() != source(). I havent fixed it because I'm not sure which one is the correct. Basically:
|
commented Jan 25, 2016
If you have not commented these tests. Please, can you answer?:
|
commented Jan 25, 2016
I did not look at (or change) the code at all yet, just built and tried to run it as-is. But I think I see the main problem. The self-test requires (off the top of my head) that the output of source() exactly matches the original ciphertext as it looked after split(). I need to look closer to this but in the end it's very trivial and, like you said, mostly about deciding what to do. |
commented Jan 25, 2016
Ok, I decided that the last 32 bits are alwas zero (in source and self text cipher text). Does it work to you? It does here, on super and well. |
commented Jan 26, 2016
That works. But I suppose it now needs input hashes padded with zeros? That is inconvenient for user. I presume the native format is simply 32 characters of hex. |
commented Jan 26, 2016
OTOH the currently committed format has the same padding.. |
commented Jan 26, 2016
I committed it (bleeding dubbed it c5d7b91 but it's the same commit). We'll see what to do with that padding in the end. |
commented Jan 26, 2016
No, it doesn't. You can crack a pure RAW1 hash using AxCrypt. Only self test hashes have to be padded. |
commented Jan 26, 2016
Yes but I meant just 128 bits of input, as in |
commented Jan 26, 2016
We probably should 'fail' in valid for hashes that are 40 byte hex, and top 8 bytes are NOT 0. |
commented Jan 28, 2016
Unless zero-padded 40-byte ones are seen in the wild, we shouldn't support them at all. Only 32-byte truncated ones. |
commented Jan 28, 2016

The original 'how to' page listed to append 0 bytes to the 32 byte hex. Who knows what will be seen ITW |
commented Jan 28, 2016
I would say that clearly indicates they come as 32 byte hex. |
commented Jan 29, 2016
John The Ripper Crack Excel
Hi, sorry for the delay
you are right, but 'original' axcrypt-sha1 should be padded (see below)
Yes, they are 32 bytes hex hashes, as found in memory, but I had to pad to 40 bytes to fit raw-sha1 default implementation
That could be an option yes, but I think it should be better to only check the first 32 hex bytes (eg: you've already cracked a raw-sha1 and this one is present in your .pot, then we should be able to say 'ok this one is already cracked and is the same as the 32 hex bytes axcrypt one I try to crack' to shorten crack tests) |
John The Ripper Crack Hash Linux
commented Jan 31, 2016
John The Ripper Crack Hash
Could we add linked-in raw-sha1 to the raw-sha1 format, OR would the reverse steps be a problem since we have to check the 2nd 4 byte value ? I think the split/prepare/valid should be easy. The source would likely simply copy over from the current format. But it is the hash and cmp_*() functions which I question if we can do easily. |